Supporting you in strengthening trust through digital identity
Set-up your trust-ecosystem in your specific industry.
I'm interested
Concept
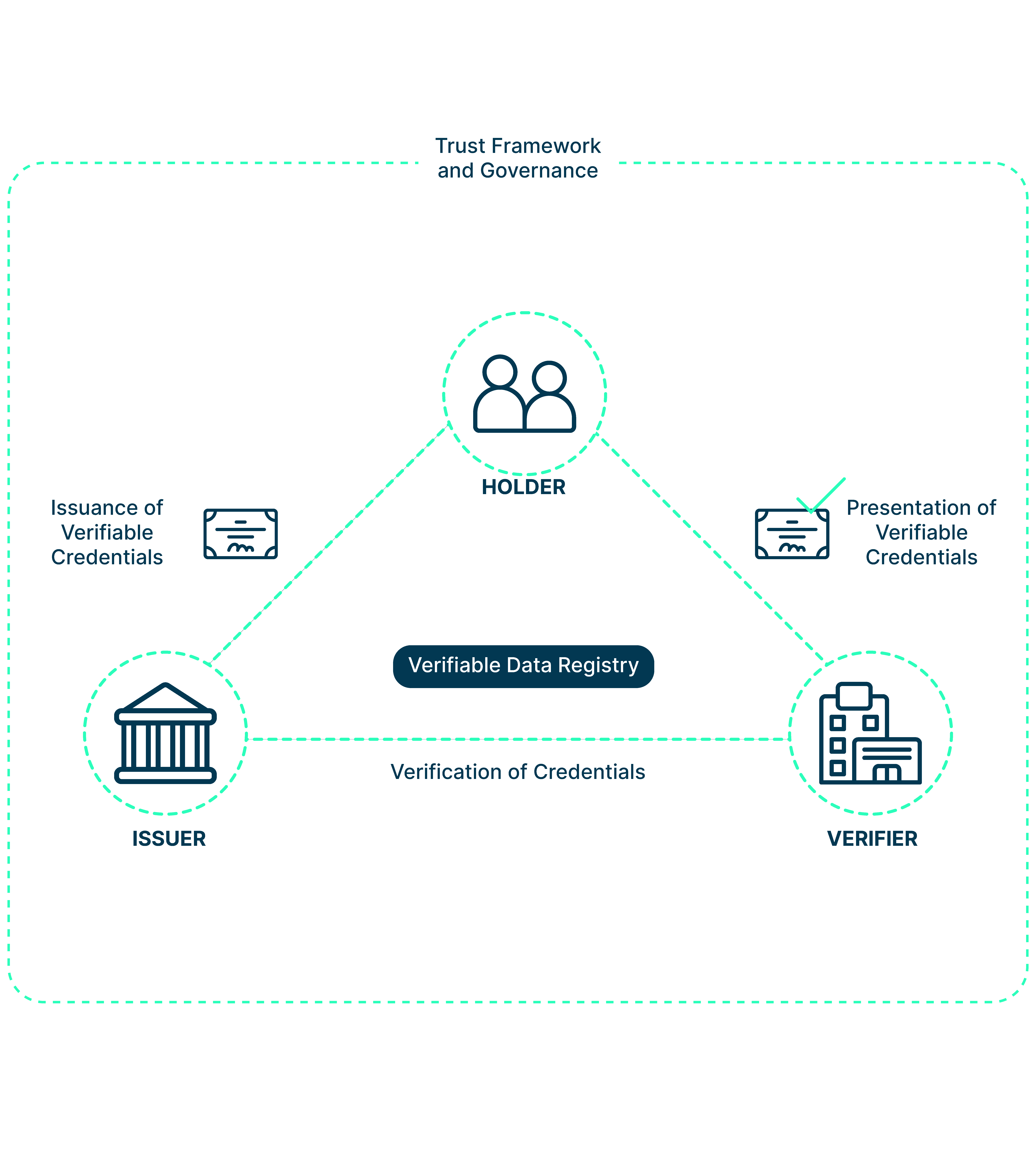
Trust Triangle
Digital Identity centers on three key actors: issuer, holder, and verifier, forming the Trust Triangle.
Issuer
- Issues verifiable credentials based on the specific use case to a holder. Usually, assert claims about an enterprise or product and is a trusted party in its ecosystem, e.g. a government authority.
Holder
- Holds his verifiable credentials, controls them, and shows them on request. Usually bound to an enterprise, object, or individuals.
Verifier
- Requests presentations of verifiable credentials and verifies them cryptographically to assure that data has not been tampered with. Uses data to support its business processes. Usually bound to enterprises or individuals.
Trust Framework
- Trust framework defines the guiding principles and governance applied in an ecosystem, sets the rules to be fulfilled to join the ecosystem, (e.g. to be an issuer) and sets technical standards to follow.
GET INVOLVED IN THESE ECOSYSTEMS WITH SPHERITY'S CLOUD IDENTITY WALLET SOLUTIONS





ECOSYSTEM
Build a trusted ecosystem with us at every step
Explore what's included in our services
Explore the possibilities of decentralized identity for your ecosystem
- Let´s jointly develop use cases and business process journeys. Understand the potentials of digital identity technology. We support you building an impactful ecosystem.
Build your MVP or field test using decentralized identity
- We can easily set-up a MVP or field test with you. Use our ready-built identity wallet technology to easily test your use case and integrate with your existing IT systems.
Define the standards, architecture and trust framework
- Ready to detail the trust ecosystem on technical level? We support you detailing architecture handbooks, technical specification or conformance criteria.
Get prepared for production
- Close to production? Integrate securely with our APIs with any existing IT systems. We support you with production grade identity wallet cloud service.
Our Technology
Decentralized Identifiers
- Unique, permanent, discoverable and verifiable decentralized identifier can serve as a lifetime address.
Verifiable Credentials
- Secure storage of verifiable data, that are cryptographically secure, privacy-respecting, and machine-readable.
Access Management
- Configuration service for access control and privacy of data with role based access management (RBAC) & attribute based access management (ABAC)
Implementation partners
We build Gaia-X compatible Organisational Credential Manager (OCM) and Personal Credential Manager (PCM) for your data space projects.